Efficient Algorithms for Demand-Aware Networks and a Connection to Virtual Network Embedding
Abstract
Emerging optical switching technologies enable demand-aware datacenter networks, whose topology can be flexibly optimized toward the traffic they serve. This paper revisits the bounded-degree network design problem underlying such demand-aware networks. Namely, given a distribution over communicating node pairs (represented has a demand graph), we want to design a network with bounded maximum degree (called host graph) that minimizes the expected communication distance.
We improve the understanding of this problem domain by filling several gaps in prior work. First, we present the first practical algorithm for solving this problem on arbitrary instances without violating the degree bound. Our algorithm is based on novel insights obtained from studying a new Steiner node version of the problem, and we report on an extensive empirical evaluation, using several real-world traffic traces from datacenters, finding that our approach results in improved demand-aware network designs. Second, we shed light on the complexity and hardness of the bounded-degree network design problem by formally establishing its NP-completeness for any degree. We use our techniques to improve prior upper bounds for sparse instances.
Finally, we study an intriguing connection between demand-aware network design and the virtual networking embedding problem, and show that the latter cannot be used to approximate the former: there is no universal host graph which can provide a constant approximation for our problem.
Keywords and phrases:
demand-aware networks, algorithms, virtual network embeddingCopyright and License:
2012 ACM Subject Classification:
Theory of computation Routing and network design problems ; Networks Data center networksRelated Version:
Demand-Aware Network Design with Steiner Nodes and a Connection to Virtual Network EmbeddingFunding:
This work is supported by the European Research Council (ERC) under grant agreement No. 864228 (AdjustNet), 2020-2025.Editors:
Silvia Bonomi, Letterio Galletta, Etienne Rivière, and Valerio SchiavoniSeries and Publisher:
 Leibniz International Proceedings in Informatics, Schloss Dagstuhl – Leibniz-Zentrum für Informatik
Leibniz International Proceedings in Informatics, Schloss Dagstuhl – Leibniz-Zentrum für Informatik
1 Introduction
With the popularity of data-centric applications and artificial intelligence, the traffic in datacenters is growing explosively. Accordingly, over the last years, significant research efforts have been made to render datacenter networks and other distributed computing infrastructure more efficient and flexible [28].
An intriguing approach to improve performance in networked and distributed systems, is to make them more demand-aware. In particular, emerging optical communication technologies allow to dynamically change the topology interconnecting the datacenter racks, according to the workload they currently serve [36, 22]. But also virtualization technologies enable demand-awareness, e.g., by allowing to flexibly embed a workload (e.g., processes or virtual machines) on a given infrastructure [26].
Such demand-awareness is attractive as empirical studies (e.g., from Google [36], Microsoft [12], Facebook [17]) show that communication traffic features significant spatial locality, which can be exploited for optimization [4]. For example, in a demand-aware network, frequently communicating nodes (e.g., a pair of racks in a datacenter) can be placed topologically closer, reducing communication costs and hence improving the overall performance. However, the underlying algorithmic problem of such demand-aware networks is still not well understood today.
This paper revisits the design of efficient demand-aware networks, and in particular the bounded-degree network topology design problem [8]: given a traffic matrix describing the communication demand between pairs of nodes, find a network topology (i.e., a graph) which “serves this traffic well.” Informally, the network interconnecting the nodes should be demand-aware in the sense that it provides short paths between frequently communicating node pairs, minimizing the number of hops travelled per bit. The degree bound is motivated by practical constraints and scalability requirements: reconfigurable switches typically have a limited number of ports. For example, reconfigurable links based on moving lasers or mirrors require space, and each optical circuit switch provides a single matching (i.e., degree 1 per node), hence typically limiting the degree to a small constant (e.g., 16) [24].
Bounded network design.
To formalise the goal of demand-aware network design, we adopt the framework introduced by Avin et al. [7, 8]. Specifically, in the bounded-degree demand-aware network design problem (or bounded network design problem for short), we are given a degree bound , a node set and a probability distribution over possible edges111We note that compared to the original formulation of the problem given by Avin et al. [7, 8], we define the demand distribution over undirected edges instead of directed edges. However, one may easily observe that the two formulations are equivalent: adding the demands on two opposite directed edges to a single undirected edge or splitting the demand of an undirected edge into equal demands on the two corresponding directed edges results in the same objective function. over set . The task is to find a graph with maximum degree minimizing the expected path length
| (1) |
where denotes the (hop) distance between and in . We interpret the edges with non-zero probability as forming a graph that we will refer to as a demand graph. We call the edges of the demand graph demand edges. The graph obtained as a solution is called the host graph.
State of the art and challenges.
Avin et al. [7, 8], in addition to introducing the bounded-degree network design problem, give approximation algorithms for sparse and other restricted demand distributions. This line of work is continued by Peres and Avin [34], who use square roots of graphs to obtain improved approximation algorithms for sparse distributions. The problem is also related to demand-aware data structures, such as biased binary search trees [38]. There already exists much follow-up work, e.g., on designs accounting for robustness [6], congestion [9], or scenarios where the demand-aware network is built upon a demand-oblivious network [10, 19], among many others [24, 35].
However, in terms of solving bounded-degree network design problem for general demand distributions, existing solutions face a major challenge, namely that the maximum degree of their produced host graphs depends on the density of the demand graph. More specifically, the approximation algorithms of [7, 8, 34] are what we will henceforth call demand balancing algorithms: if the demand graph has average degree , then the output host graph will have maximum degree . Considering that the degree bound represents the physical limitations of the network hardware, solutions of the demand balancing algorithms are not feasible for .
Further, we note that the computational complexity of the bounded-degree network design problem is not fully understood. Avin et al. [7, 8] note that for and connected demand graphs, the problem is equivalent to minimum circular arrangement problem and thus NP-hard. However, for general without additional assumptions, the existing literature does not give an NP-completeness proof.
Other related work.
Demand-aware networks are motivated by their applications in datacenters, where reconfigurable optical communication technologies recently introduced unprecedented flexibilities [22, 23, 41, 16, 39, 42, 25, 11, 2]. Demand-aware networks have also been studied in the context of virtualized infrastructures, and especially the virtual network embedding problem has been subject to intensive research over the last decade [18, 37, 14, 26].
Our contributions.
We make the following contributions. We present the first polynomial-time heuristic algorithm for computing bounded-degree network designs for general demand distributions, which guarantee that the degree bound is not violated (henceforth referred to as fixed-degree heuristic). This algorithm is based on solving a high-weight subproblem using an approximation algorithm for a variant of the original problem, as we will discuss below, and provably provides a valid solution for the bounded network design problem on all instances. We report on an extensive empirical evaluation, using several real-world traffic traces from datacenters. We compare our algorithm to simple solutions based on random trees and graphs as well as several simple greedy heuristics, and show that it is more reliable and produces solutions with smaller effective path lengths.
We introduce and study a variant of the bounded network design problem, in a resource augmentation model where we are allowed to use Steiner nodes in addition to the nodes of the demand graph. This approach is motivated by existing bicriteria algorithms in the literature on demand-aware network designs (which however allow for degree augmentation), and it turns out to be useful to overcome some of the limitations of existing approaches to the original bounded network design problem.
Formally, in the bounded network design problem with Steiner nodes, we are given a degree bound , a node set and a probability distribution over possible edges over set as before. The task is to find a graph with maximum degree , where is an arbitrary set disjoint from , minimizing the expected path length (1). We refer to nodes in as Steiner nodes.
We show that this variant of bounded network design can be approximated within factor in polynomial time, using elegant techniques from coding theory. The approximation algorithm will further be useful in designing various other algorithms for the standard version of bounded network design.
Interestingly, we can use our approximation algorithm for bounded network design with Steiner nodes to obtain an improved demand balancing algorithm for bounded network design without Steiner nodes: given an demand distribution with average degree , our algorithm computes a host graph with maximum degree at most and a expected path length within constant factor of the expected path length of the optimal degree- host graph. This provides better guarantees in both parameters than the existing algorithms of Avin et al. [7, 8] and Peres and Avin [34], which we also demonstrate via experimental evaluation.
A second main objective in this work is to settle the computational complexity of the bounded-degree network design problem. We show that the problem is indeed NP-complete for any fixed degree bound , and this also holds for the variant with Steiner nodes.
We further explore an intriguing connection between the problem of designing demand-aware network topologies and the virtual network embedding problem, where the demand graph can be placed on a given (demand-oblivious) network in a demand-aware manner. In particular, perhaps surprisingly at first sight, we show that the latter does not provide good approximations for the topology design problem: given any bounded-degree network (e.g., an expander graph) chosen in a demand-oblivious manner, there exist demands for which the optimal embedding into this network gives an expected path length that is an factor more than the expected path length on the optimal host graph, for networks of size .
As a contribution to the research community and to facilitate future work, we made available our simulation source code at https://github.com/inet-tub/DAN-balancing.
2 Preliminaries
Basic notation.
Let be a node set and a probability distribution given as input for the bounded network design problem. For nodes , we define
Entropy.
Let be a random variable with a finite domain . Recall that the entropy and the base- entropy of , respectively, are
| and |
For any , we have . When is distributed according to , we abuse the notation by writing for the entropy of .
For random variables and with finite domains and , respectively, the (base-) entropy of conditioned on is
Entropy bound on trees.
Consider a setting where we have a root node , a set of nodes , and demands between the root and nodes in given by a probability distribution , i.e., demand between and is . Suppose we want a tree rooted at and including all nodes of such that the expected path length between and , i.e., is minimized. It is known that this is closely related to the entropy .
Lemma 1 ([8, 30]).
Let be a set of nodes and let be a probability distribution. Then for any -ary tree with root and node set including , it holds that
Note that the above lemma covers cases where nodes in can appear as either internal nodes or as leaves. If nodes in are required to appear as leaves only, then this question is equivalent to asking for optimal prefix codes.
Entropy bound on graphs.
For the bounded network design problem, both with and without Steiner nodes, we use the following result to lower bound the cost of an optimal solution.
Theorem 3 ([8]).
Assume we have a degree bound , a node set and a probability distribution over possible edges over set . Then for any graph with maximum degree , the expected path length between nodes of satisfies
Note that while there appears to be a factor in the above inequality that is not present in the original formulation of Avin et al. [8]; this is simply due to the fact that we define the demand distribution over undirected edges rather than directed edges.
3 Hardness and lower bounds
3.1 NP-completeness
Consider the bounded network problem with integer weights in its decision form: is there a solution with expected path length at most some given value ? We show hardness for both the versions with and without Steiner nodes.
Theorem 4.
Bounded network design and bounded network design with Steiner nodes are NP-complete for any fixed .
Due to space constraints, we describe all the details in Appendix A. Here, we briefly comment on some main ideas. A first detail is that we verify that the version with Steiner nodes is in fact in NP; the subtlety here is that we need to show that a polynomial number of Steiner nodes suffices for an optimal solution.
For , Steiner nodes are clearly not helpful, and so both variants are the same. NP-completeness follows easily from a variant of the minimum linear arrangement problem, namely undirected circular arrangement.
For , we have to work harder. In Appendix A we give a reduction from vertex cover on 3-regular graphs utilizing multiple gadgets in the construction.
3.2 A lower bound for a universal host graph
We now return to the question of approximation algorithms for bounded network design without Steiner nodes. One possible approach one might consider is choosing a “universal” host graph of maximum degree , e.g., a -regular expander, and the solving the problem by embedding the demands into this universal host graph. We show in this section that this approach cannot yield a constant-factor approximation algorithm.
We will restrict our attention to uniform demand functions, and will henceforth simply refer to demand graphs with the implicit understanding that the demand function is uniform. The precise question we now want to ask is whether there exists a host graph such that the following holds: given a demand graph with vertices, which has an optimal embedding into a host graph (with maximum degree ) of expected path length , we have an embedding into of expected path length .
Theorem 5.
Let . For any host graph of size and maximum degree , there exists some demand graph with maximum degree for which the optimal embedding of into has expected path length , where constants depending on are hidden in the .
Note that such a demand graph trivially has an embedding into a graph of maximum degree and with expected path length 1; simply use itself.
Proof.
We consider ; the claim is obvious for , as the only connected host graphs are the -path and the -cycle, and a demand graph consisting of two cycles of length does not have a good embedding into either.
Let be the collection of -regular graphs on . We assume from hereon that is even, since otherwise is empty. Standard results allow us to bound . Asymptotically, the number of -regular graphs (ignoring constants depending on ) is (see [13])
Applying this gives us the lower bound
Suppose that for every graph on with maximum degree , there is some embedding (that is, a permutation) that embeds into with an average stretch of at most . Let , for any permutation of . There must be some permutation for which
As long as , this is at least .
We will restrict our attention to going forward. Without loss of generality, we can assume is the identity.
Let be the graph where whenever the shortest path distance between and in at most .
Lemma 6.
has fewer than edges.
Proof.
For each , just from the degree bound for we deduce that there are less than nodes within distance of . From our choice of , this means that has at most edges.
We consider every possible subgraph of . For each such , let
Since there are at most subgraphs of , it follows that there exists some subgraph of for which
| (2) |
For each , given that the average stretch of is at most , we have by Markov’s inequality that at most fraction of the edges of have stretch more than . That is, . This means we can describe in an efficient way: its edge set consists of , along with at most other edges.
Considering that we can describe every in such a way, we deduce that is at most the number of ways of choosing a subset of at most edges from the collection of pairs. Hence
This contradicts (2).
4 Approximation with Steiner nodes
In this section, we give a constant-factor approximation algorithm for the bounded network design with Steiner nodes. Let be the degree bound, the set of nodes and the probability distribution given as input. Let denote the number of demand edges.
Approximation algorithm.
We now present the approximation algorithm itself. The algorithm constructs the host graph in two simple steps: first, for each node separately, we construct a Huffman tree for the distribution , i.e., the conditional distribution of the other endpoint given that is included in the demand edge. Second, we connect these trees together to obtain the final host graph.
In more detail, the algorithm constructs the host graph as follows:
-
1.
For each node , let be the -ary Huffman tree for probability distribution , ignoring any probabilities of . Denote the leaf node corresponding to probability as , and let be the distance from to in .
In the special case that for some , we take to be a tree with a root and a single leaf instead of the trivial tree.
-
2.
For each pair with , we add an edge between the parent of in and the parent of in , and remove the nodes and .
See Figure 1 for illustration.
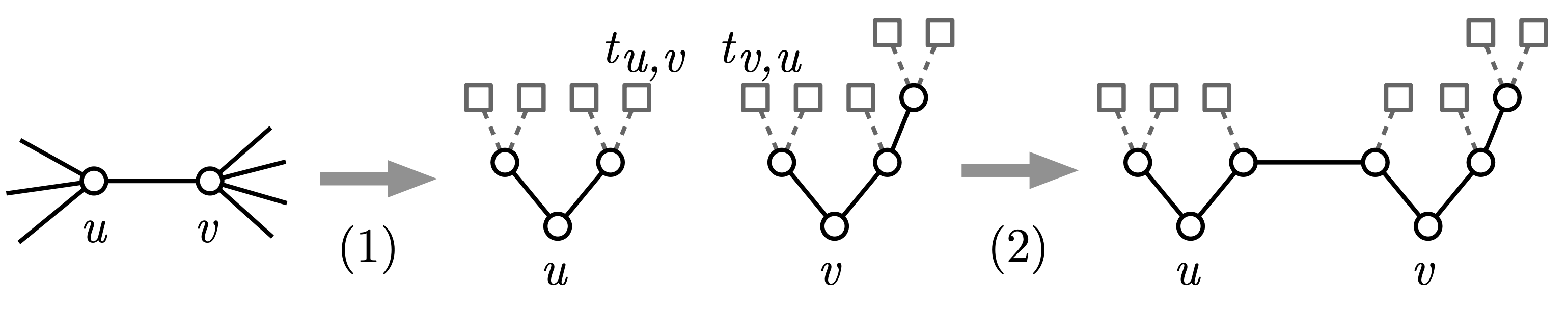
Time complexity.
To analyze the time complexity of the approximation algorithm, we first observe that constructing the Huffman tree in Step (1) for node takes time, where is the degree of in the demand graph. We have
and thus constructing Huffman trees for all nodes takes time in total. Step (2) can clearly also be implemented in time, so the total time complexity is .
Cost of solution.
Consider a graph as constructed above. By construction, we have
for all . Thus, the expected path length between nodes in in is
The expected path length of an optimal solution is or greater by Theorem 3. Comparing this to the expected path length upper bound on , we have that the approximation factor of the algorithm is . Note that is at most for all , and at most for all .
Number of nodes.
Let and let be the number of non-zero entries in . We now want to analyze the total number of nodes in in the graph given by the above algorithm.
Fact 7 (e.g. [27]).
Given a -ary Huffman tree , the leaves can be rearranged so that all internal nodes of have exactly children, with the exception of one internal node located at the maximum distance from the root. This node has at least children.
Fact 8.
A full -ary tree with leaves has internal nodes.
Now consider the Huffman tree constructed in Step (1) of the algorithm. Let be the arity of the Huffman trees. Denoting the outdegree of in by , and assuming , we have that has leaves. By Fact 7, we can turn into a full -ary tree by adding at most leaves, which has leaves. By Fact 8 it has at most
internal nodes; this is also an upper bound for the number of internal nodes in .
In the special case , the above bound does not hold. However, we can use a slightly looser bound of to cover all cases.
Since the leaf nodes of the Huffman trees are deleted in Step 2 of the algorithm, the total number of nodes in is the total number of internal nodes in these trees – note that the roots of the trees correspond to the original nodes in . Thus, the number of nodes in is at most
| (3) |
5 Applications
This section discusses applications of our approach. First, we will use it to derive improved approximation bounds for the original demand-aware network design problem which results in a constant-factor approximation for the case where the maximum degree is close the average degree of the demand graph. Second, we show how it can be used to obtain efficient heuristics.
5.1 Improved approximation algorithm for demand balancing
In this section, we use the ideas from our approximation algorithm for bounded network design with Steiner nodes to design a demand balancing algorithm in the spirit of the results of Avin et al. [8]. That is, we consider a demand graph with average degree , but with possibly some nodes with very high degree, and we want to design a host graph without Steiner nodes that has maximum degree close to .
Here, we give an improved version of Theorem 4 of [8], showing how to construct a host graph with maximum degree and better expected path length guarantees. Specifically, we improve the maximum degree guarantee from to and the expected path length guarantee by a factor of , which results in a constant-factor approximation.
5.1.1 Algorithm
For technical convenience, we assume is an integer and is divisible by . We say that a node is a high-degree node if its degree in the demand graph satisfies , and otherwise we say it is a low-degree node. By Markov’s inequality, the number of high-degree nodes is at most .
For each node , we say that the up to demand graph edges for which are highest are the high-demand edges for , and the rest of the edges are low-demand edges for . Note that only heavy nodes have low-demand edges.
We now construct the host graph in two steps as follows.
Step 1: Low-demand trees.
For a heavy node , let and be the set of neighbours of in the demand graph such that is low-demand and high-demand, respectively. Define a distribution on by selecting an arbitrary node and setting
As in Section 4, we construct a -ary Huffman tree for terminal set wrt. the probabilities . As before, denote the leaf node corresponding to probability as , and let be the distance from to in .
We repeat the construction for all heavy nodes, and map the internal nodes of the trees injectively to nodes of so that root of the tree for is . We then add all edges of the tree to the routing graph . This is always possible, since by applying (3) with , , and , we have that there are at most internal nodes, including the roots, in the constructed trees.
Step 2: Connecting edges.
Now consider edge in the demand graph. There are three cases to consider:
-
1.
Edge is high-demand for both and . In this case, we add edge to .
-
2.
Edge is low-demand for both and . In this case, we add an edge from the parent node of to the parent node of to .
-
3.
Otherwise, without loss of generality, edge is high-demand for and low-demand for . In this case, we add an edge from to the parent of to .
5.1.2 Analysis
Time complexity.
By the same argument as in Section 4, we can see that computing the high-demand edges and building the Huffman trees for low-demand edges can be done in time in total. All other steps of the algorithm can be implemented with at most time.
Maximum degree.
Low-demand trees constructed in Step 1 have arity , and thus contribute at most to the degree of each node. This includes edges added for low-demand edges. Moreover, each node has at most edges added for handling high-demand edges, for a total of .
Expected path length.
Here we show that the expected path length in is at most . First, let us recall the grouping rule for entropy.
Lemma 9.
Let be a distribution, and let be a distribution defined by for , and . Then
It follows immediately from Lemma 9 that for a heavy node we have for any .
Now consider a non-zero demand . There are four cases to consider for the distance between and in :
-
1.
: distance is .
-
2.
: distance is .
-
3.
: distance is .
-
4.
: distance is .
Let be the set of demand edges, i.e., edges with non-zero demand. For a predicate , denote by a function that is if predicate is true, and otherwise. The expected path length in is now
By re-grouping terms, this is equal to
By omitting the last negative term, and rearranging further, this is at most
For fixed , we have
Thus, the expected path length in is at most
In comparison, by Theorem 3 the expected path length for degree- host graphs is at least , meaning that is a constant-factor approximation for the optimal degree- host graph.
5.2 Fixed-degree heuristics
The main challenge of our methods, as well as the prior work, is that we do not have approximation algorithms for bounded network designs that strictly respect a given arbitrary degree bound, without using additional resources such as Steiner nodes. However, in practice we expect that parameters such as the degree bound and number of Steiner nodes are limited by the physical properties of the network infrastructure, so solutions respecting these limitations would be required.
We describe a few heuristics which although do not have any guarantees on the quality of their solution, nevertheless appeared to have worked well in our experiments.
Fixed-degree heuristic.
We choose a subset of edges from the demand graph with large weights and use the Steiner node insertion algorithm to construct a DAN with maximum degree for these edges. The number of picked edges is low enough to guarantee that we only need at most nodes for the construction of the DAN. Lastly, a randomly chosen (almost) -regular graph is overlaid on top of this DAN.
Random tree and random graph.
We simply pick a randomly chosen -ary tree or (nearly) regular graph as the demand aware graph. This is oblivious to the actual demand, but tends to have low diameter.
Greedy edge deletion.
We initially use the demand graph as the DAN. We iteratively delete edges of low weight incident on vertices with degree greater than the degree bound . Deleting an edge may disconnect the graph and result in infinite expected path length. We do not delete edges if it would disconnect the graph, but as a result we may violate the degree bound , in which case we say the algorithm failed.
Greedy edge selection.
We start with an empty DAN and iteratively add edges from the demand graph starting with the ones with highest weight. We do not add an edge if it would exceed the degree bound . The algorithm may fail to construct a connected graph.
6 Empirical Evaluation
In this section we complement our theoretical insights with empirical evaluations using datacenter traces.
6.1 Methodology
All presented algorithms in this paper were implemented and evaluated in simulations. Furthermore, we provide comparisons to other methods such as the algorithm for sparse distributions from Theorem 4 by Avin et al. [8], which we will refer to as the Helper algorithm, and a -root graph approach by Peres and Avin [34], where , where is the maximum degree in the demand graph, which we will refer to as the Split&Join algorithm. For a full overview of the algorithms used in the experiments see Table 1.
Unfortunately, obtaining optimal solutions for our problem using integer linear programming was not feasible. We need binary variables representing each possible edge in the output graph and for modeling the expected path length in the resulting graph we needed a cubic number of integer variables. Solving these ILPs was feasible for only very small instances.
| Name | Shorthand | Ref. | Steiner nodes | as input |
|---|---|---|---|---|
| Steiner Node Insertion | SNI | Section 4 | yes | yes |
| Demand Balancing | DB | Section 5.1 | no | no |
| Split&Join | S&J | Split&Join [34] | no | no |
| Helper | Help | Theorem 4 in [8] | no | no |
| Fixed-degree | Fix-Deg | Section 5.2 | no | yes |
| Random Tree | Rnd-Tree | Section 5.2 | no | yes |
| Random Graph | Rnd-Graph | Section 5.2 | no | yes |
| Greedy Edge Deletion | GED | Section 5.2 | no | yes |
| Greedy Edge Selection | GES | Section 5.2 | no | yes |
Dataset.
For the experiments we used the real-world datacenter trace collection from Avin et al. [5] that was also used by previous works [10, 34, 8]. These traces contain temporal data, specifically source, destination and timestamps of communicating nodes. To adapt these traces to our demand graph input format, we create an edge between two communicating nodes and set its weight equal to number of times the nodes communicated. The weights are normalized so that this can be interpreted as a communication distribution (demand). In Appendix B in Table 4 some selected parameters of these instances are summarized.
6.2 Results
We divide the results of the experiments into three groups, based on the algorithms which they involve, similar to the grouping in Table 1.
Sparse heuristics.
We first focus our attention on the bounded network design heuristics for which the maximum degree is a function of the input demand graph and cannot be specified by the user. In Table 2 properties of the resulting host graphs computed by these algorithms on our network trace dataset are presented. The Helper heuristic appeared to have the highest expected path length and second largest maximum degree compared to the other three approaches. In contrast, the Demand Balancing heuristic achieved the lowest expected path length while also having the lowest maximum degree, except for three demand graphs. For four of the ten demand graphs the expected path lengths for the Demand Balancing and Split&Join heuristics were almost a third of the expected path length of the Helper heuristic. The Split&Join heuristic achieved a low expected path length, but at the cost of having a comparatively large maximum degree, almost double that of the Demand Balancing heuristic for three demand graphs.
| Split&Join | Helper | DB | ||||
|---|---|---|---|---|---|---|
| Trace | EPL | EPL | EPL | |||
| fb-cluster-rack-A | 290 | 1.31 | ||||
| fb-cluster-rack-B | 754 | 1.05 | ||||
| fb-cluster-rack-C | 683 | 1.08 | ||||
| hpc-cesar-mocfe | 18 | 1.0 | ||||
| hpc-cesar-nekbone | ||||||
| hpc-boxlib-cns | 102 | 1.01 | ||||
| hpc-boxlib-multigrid | ||||||
| p-fabric-trace-0-1 | 143 | |||||
| p-fabric-trace-0-5 | ||||||
| p-fabric-trace-0-8 | ||||||
Fixed degree heuristics.
We next compare different heuristics for which the maximum degree is an input parameter. In Figure 2 the average expected path length over our whole dataset is plotted against the maximum degree constraint for different heuristics. It is apparent that the two heuristics that are oblivious to the demand graph, namely the Random Tree and Random Graph heuristics have the worst expected path length, which was expected to due their obliviousness to the input.
Unsurprisingly, the Random Tree heuristic is significantly worse than for example the Random Graph heuristic. The randomly constructed -ary tree has many leaves which by definition have a degree of one, and are thus poorly utilized as more edges could be inserted to improve the EPL.
In Table 3 we present results from Figure 2 for the case in more detail, and also include some results for heuristics which failed do solve some instances. For the Facebook instances the Fixed-degree heuristic has the lowest expected path length. For some demands the heuristics achieve an expected path length of almost one, whereas the Random Graph and Tree heuristics have at least double the expected path length. The Greedy Edge Deletion and Greedy Edge Selection fail on the Facebook instances.
| Trace | Fix-Deg | Rnd Graph | Rnd Tree | GED | GES |
|---|---|---|---|---|---|
| fb-cluster-rack-A | 2.6 | – | – | ||
| fb-cluster-rack-B | 2.48 | – | – | ||
| fb-cluster-rack-C | 2.69 | – | – | ||
| hpc-cesar-mocfe | |||||
| hpc-cesar-nekbone | |||||
| hpc-boxlib-cns | 1.85 | ||||
| hpc-boxlib-multigrid | |||||
| p-fabric-trace-0-1 | – | ||||
| p-fabric-trace-0-5 | 1.27 |
Steiner nodes.
Our last experiments involve the Steiner Node Insertion algorithm. Recall, that the Steiner Node Insertion algorithm is allowed to use additional nodes (Steiner nodes) that are not present in the demand graph. For a relatively low maximum degree of eight the number of new nodes used by the algorithm is sometimes even greater than . As the maximum degree increases, the expected path length decreases and so does the number of used Steiner nodes. For some traces the number of Steiner nodes remains quite high. For example, for on the second Facebook trace the algorithm used Steiner nodes.
Furthermore, in Figure 2 we compare the Steiner Node Insertion algorithm to the Fixed-degree heuristic which utilizes the Steiner Node Insertion algorithm, but does not use Steiner nodes; that is, it computes a host graph with the same vertex set as the demand graph. It can be observed that the Steiner Node Insertion algorithm achieves a slightly lower expected path length on average, but as can be seen in Table 5 (Appendix B) this is at the cost of utilizing many Steiner nodes. The Fixed-degree does not utilize Steiner nodes, but the expected path length is marginally larger.
7 Conclusion
This paper presented new approaches to designing bounded-degree demand-aware networks, leading to improved approximation algorithms as well as heuristics for variants of the problem. We also presented various hardness results and lower bounds. From the extensive empirical evaluation, we highlight our fixed-degree heuristic as a practical algorithm for bounded-degree network design problem; it is guaranteed to respect the given degree bound regardless of the demand distribution and, in experiments, achieves expected paths lengths close to optimal on real-world instances.
Our work leaves open several interesting directions for future research. In particular, it will be interesting to explore the tradeoff between approximation quality and resource augmentation. More generally, it remains open whether a constant-factor approximation algorithm exists for bounded-degree network design without augmentation.
References
- [1] Vamsi Addanki, Chen Avin, and Stefan Schmid. Mars: Near-optimal throughput with shallow buffers in reconfigurable datacenter networks. Proc. ACM Meas. Anal. Comput. Syst., 7(1), March 2023. doi:10.1145/3579312.
- [2] Daniel Amir, Nitika Saran, Tegan Wilson, Robert Kleinberg, Vishal Shrivastav, and Hakim Weatherspoon. Shale: A practical, scalable oblivious reconfigurable network. In Proceedings of the ACM SIGCOMM 2024 Conference, ACM SIGCOMM ’24, pages 449–464, New York, NY, USA, 2024. Association for Computing Machinery. doi:10.1145/3651890.3672248.
- [3] Daniel Amir, Tegan Wilson, Vishal Shrivastav, Hakim Weatherspoon, Robert Kleinberg, and Rachit Agarwal. Optimal oblivious reconfigurable networks. In Proceedings of the 54th Annual ACM SIGACT Symposium on Theory of Computing, STOC 2022, 2022. doi:10.1145/3519935.3520020.
- [4] Chen Avin, Manya Ghobadi, Chen Griner, and Stefan Schmid. On the complexity of traffic traces and implications. In Proc. ACM SIGMETRICS, 2020.
- [5] Chen Avin, Manya Ghobadi, Chen Griner, and Stefan Schmid. On the complexity of traffic traces and implications. Proceedings of the ACM on Measurement and Analysis of Computing Systems, 4(1):1–29, 2020. doi:10.1145/3379486.
- [6] Chen Avin, Alexandr Hercules, Andreas Loukas, and Stefan Schmid. rDAN: Toward robust demand-aware network designs. Information Processing Letters, 133:5–9, 2018. doi:10.1016/J.IPL.2017.12.008.
- [7] Chen Avin, Kaushik Mondal, and Stefan Schmid. Demand-aware network designs of bounded degree. In Proc. International Symposium on Distributed Computing (DISC), 2017.
- [8] Chen Avin, Kaushik Mondal, and Stefan Schmid. Demand-aware network designs of bounded degree. Distributed Computing, 33(3):311–325, 2020. doi:10.1007/S00446-019-00351-5.
- [9] Chen Avin, Kaushik Mondal, and Stefan Schmid. Demand-aware network design with minimal congestion and route lengths. IEEE/ACM Transactions on Networking, 30(4):1838–1848, 2022. doi:10.1109/TNET.2022.3153586.
- [10] Chen Avin and Stefan Schmid. Renets: Statically-optimal demand-aware networks. In Symposium on Algorithmic Principles of Computer Systems (APOCS), pages 25–39. SIAM, 2021. doi:10.1137/1.9781611976489.3.
- [11] Chen Avin and Stefan Schmid. Renets: Statically-optimal demand-aware networks. In Proc. SIAM Symposium on Algorithmic Principles of Computer Systems (APOCS), 2021.
- [12] Hitesh Ballani, Paolo Costa, Raphael Behrendt, Daniel Cletheroe, Istvan Haller, Krzysztof Jozwik, Fotini Karinou, Sophie Lange, Kai Shi, Benn Thomsen, et al. Sirius: A flat datacenter network with nanosecond optical switching. In Proceedings of the Annual conference of the ACM Special Interest Group on Data Communication on the applications, technologies, architectures, and protocols for computer communication, pages 782–797, 2020.
- [13] Edward A Bender and E. Rodney Canfield. The asymptotic number of labeled graphs with given degree sequences. Journal of Combinatorial Theory, Series A, 24(3):296–307, 1978. doi:10.1016/0097-3165(78)90059-6.
- [14] NM Mosharaf Kabir Chowdhury, Muntasir Raihan Rahman, and Raouf Boutaba. Virtual network embedding with coordinated node and link mapping. In IEEE INFOCOM 2009, pages 783–791. IEEE, 2009.
- [15] Thomas M. Cover and Joy A. Thomas. Elements of information theory. Wiley-Interscience, 2006.
- [16] Fred Douglis, Seth Robertson, Eric Van den Berg, Josephine Micallef, Marc Pucci, Alex Aiken, Maarten Hattink, Mingoo Seok, and Keren Bergman. Fleet—fast lanes for expedited execution at 10 terabits: Program overview. IEEE Internet Computing, 25(3):79–87, 2021. doi:10.1109/MIC.2021.3075326.
- [17] Nathan Farrington and Alexey Andreyev. Facebook’s data center network architecture. In 2013 Optical Interconnects Conference, pages 49–50. IEEE, 2013.
- [18] Aleksander Figiel, Leon Kellerhals, Rolf Niedermeier, Matthias Rost, Stefan Schmid, and Philipp Zschoche. Optimal virtual network embeddings for tree topologies. In Proceedings of the 33rd ACM Symposium on Parallelism in Algorithms and Architectures, pages 221–231, 2021. doi:10.1145/3409964.3461787.
- [19] Aleksander Figiel, Darya Melnyk, Andre Nichterlein, Arash Pourdamghani, and Stefan Schmid. Spiderdan: Matching augmentation in demand-aware networks. In SIAM Symposium on Algorithm Engineering and Experiments (ALENEX), 2025.
- [20] M. R. Garey, D. S. Johnson, and L. Stockmeyer. Some simplified NP-complete graph problems. Theoretical Computer Science, 1(3):237–267, 1976. doi:10.1016/0304-3975(76)90059-1.
- [21] Michael R. Garey and David S. Johnson. Computers and Intractability. W.H. Freeman and Company, 1979.
- [22] Monia Ghobadi, Ratul Mahajan, Amar Phanishayee, Nikhil Devanur, Janardhan Kulkarni, Gireeja Ranade, Pierre-Alexandre Blanche, Houman Rastegarfar, Madeleine Glick, and Daniel Kilper. Projector: Agile reconfigurable data center interconnect. In Proceedings of the 2016 ACM SIGCOMM Conference, pages 216–229. ACM, 2016. doi:10.1145/2934872.2934911.
- [23] Chen Griner, Johannes Zerwas, Andreas Blenk, Manya Ghobadi, Stefan Schmid, and Chen Avin. Cerberus: The power of choices in datacenter topology design (a throughput perspective). Proc. ACM Meas. Anal. Comput. Syst., 5(3), December 2021. doi:10.1145/3491050.
- [24] Matthew Nance Hall, Klaus-Tycho Foerster, Stefan Schmid, and Ramakrishnan Durairajan. A survey of reconfigurable optical networks. Optical Switching and Networking, 41:100621, 2021. doi:10.1016/J.OSN.2021.100621.
- [25] Navid Hamedazimi, Zafar Qazi, Himanshu Gupta, Vyas Sekar, Samir R. Das, Jon P. Longtin, Himanshu Shah, and Ashish Tanwer. Firefly: a reconfigurable wireless data center fabric using free-space optics. SIGCOMM Comput. Commun. Rev., 44(4):319–330, August 2014. doi:10.1145/2740070.2626328.
- [26] Monika Henzinger, Stefan Neumann, and Stefan Schmid. Efficient distributed workload (re-) embedding. Proc. ACM SIGMETRICS, 2019.
- [27] Stefan Höst. Information and Communication Theory. Wiley-IEEE Press, 2019.
- [28] Wolfgang Kellerer, Patrick Kalmbach, Andreas Blenk, Arsany Basta, Martin Reisslein, and Stefan Schmid. Adaptable and data-driven softwarized networks: Review, opportunities, and challenges. Proceedings of the IEEE, 107(4):711–731, 2019. doi:10.1109/JPROC.2019.2895553.
- [29] Vincenzo Liberatore. Circular arrangements. In Proc. International Colloquium on Automata, Languages, and Programming (ICALP 2002), pages 1054–1065. Springer, 2002. doi:10.1007/3-540-45465-9_90.
- [30] Kurt Mehlhorn. Nearly optimal binary search trees. Acta Informatica, 5(4):287–295, 1975. doi:10.1007/BF00264563.
- [31] William M Mellette, Rajdeep Das, Yibo Guo, Rob McGuinness, Alex C Snoeren, and George Porter. Expanding across time to deliver bandwidth efficiency and low latency. In Proc. 17th USENIX Symposium on Networked Systems Design and Implementation (NSDI 20), pages 1–18, 2020. URL: https://www.usenix.org/conference/nsdi20/presentation/mellette.
- [32] William M Mellette, Rob McGuinness, Arjun Roy, Alex Forencich, George Papen, Alex C Snoeren, and George Porter. Rotornet: A scalable, low-complexity, optical datacenter network. In Proceedings of the Conference of the ACM Special Interest Group on Data Communication, pages 267–280. ACM, 2017. doi:10.1145/3098822.3098838.
- [33] Alistair Moffat. Huffman coding. ACM Computing Surveys, 52(4), 2019. doi:10.1145/3342555.
- [34] Or Peres and Chen Avin. Distributed demand-aware network design using bounded square root of graphs. In IEEE Conference on Computer communications (INFOCOM). IEEE, 2023. doi:10.1109/INFOCOM53939.2023.10228932.
- [35] Arash Pourdamghani, Chen Avin, Robert Sama, Maryam Shiran, and Stefan Schmid. Hash & adjust: Competitive demand-aware consistent hashing. In International Conference on Principles of Distributed Systems (OPODIS), 2024. doi:10.4230/LIPIcs.OPODIS.2024.24.
- [36] Leon Poutievski, Omid Mashayekhi, Joon Ong, Arjun Singh, Mukarram Tariq, Rui Wang, Jianan Zhang, Virginia Beauregard, Patrick Conner, Steve Gribble, et al. Jupiter evolving: transforming google’s datacenter network via optical circuit switches and software-defined networking. In Proc. ACM SIGCOMM 2022 Conference, pages 66–85, 2022.
- [37] Matthias Rost and Stefan Schmid. Virtual network embedding approximations: Leveraging randomized rounding. IEEE/ACM Transactions on Networking, 27(5):2071–2084, 2019. doi:10.1109/TNET.2019.2939950.
- [38] D.D. Sleator and R.E. Tarjan. Self-adjusting binary search trees. Journal of the ACM (JACM), 32(3):652–686, 1985. doi:10.1145/3828.3835.
- [39] Min Yee Teh, Zhenguo Wu, and Keren Bergman. Flexspander: augmenting expander networks in high-performance systems with optical bandwidth steering. IEEE/OSA Journal of Optical Communications and Networking, 12(4):B44–B54, 2020. doi:10.1364/JOCN.379487.
- [40] Tegan Wilson, Daniel Amir, Nitika Saran, Robert Kleinberg, Vishal Shrivastav, and Hakim Weatherspoon. Breaking the vlb barrier for oblivious reconfigurable networks. In Proceedings of the 56th Annual ACM Symposium on Theory of Computing, STOC 2024, 2024. doi:10.1145/3618260.3649608.
- [41] Johannes Zerwas, C Gyorgyi, A Blenk, Stefan Schmid, and Chen Avin. Duo: A high-throughput reconfigurable datacenter network using local routing and control. In Proc. ACM SIGMETRICS, 2023.
- [42] Mingyang Zhang, Jianan Zhang, Rui Wang, Ramesh Govindan, Jeffrey C Mogul, and Amin Vahdat. Gemini: Practical reconfigurable datacenter networks with topology and traffic engineering. CoRR, 2021. arXiv:2110.08374.
Appendix A Hardness of bounded-degree network design
Decision version of bounded-degree network design.
In this section, we show that the decision versions of bounded-degree network design, with or without Steiner nodes, is NP-complete for any fixed degree bound . Formally, the decision version bounded of bounded-degree network design is defined as follows – note that we consider an integer-weighted version of the problem to sidestep considerations regarding encoding of small fractional number:
- Instance:
-
A set with , a weight function , positive integers and .
- Question:
-
Is the a graph such that maximum degree of is at most and
where denotes the distance between and in .
The decision version of bounded-degree network design with Steiner nodes is defined analogously:
- Instance:
-
A set with , a weight function , positive integers and .
- Question:
-
Is there a graph such that , the maximum degree of is at most , and
where denotes the distance between and in ?
While it is immediately clear that bounded-degree network design without Steiner nodes is in NP, it is not a priori clear that the version with Steiner nodes always has optimal host graphs of polynomial size. However, not surprisingly this is indeed the case:
Lemma 10.
For any instance of bounded-degree network design problem with Steiner nodes, there is a solution with optimal effective path length and at most a polynomial number of Steiner nodes.
Proof.
For , one can immediately observe that there is a solution with optimal effective path length without Steiner nodes, as we can replace any degree- Steiner node with an edge. Thus, assume and let be a host graph with optimal effective path length for an instance of bounded-degree network design with Steiner nodes. Moreover, assume that is minimal in the sense that any proper subgraph of has larger effective path length.
Let be arbitrary pair of nodes with non-zero demand between them and distance in , and consider the shortest path between and in . Let be an another pair of nodes with non-zero demand between them, possibly including either or but not both. We say that an edge with exactly one endpoint on is critical for and if removing it from would increase the distance between and .
Consider a shortest path between and that intersects with , and let and be the first and the last node on that is also on , respectively. As both and are shortest paths, the distance between and must be the same along and . It follows that only and can be critical for and , if they exist. Moreover, a critical edge must be on all shortest paths between and , so there can be at most two critical edges for and .
Now consider an arbitrary edge with exactly one endpoint on . By minimality of , deleting would increase the distance between some pair ; thus, edge is critical for some and . By choice of , it follows that all edges with exactly one endpoint on are critical for some and . By above argument, there are at most critical edges, and thus at most that many edges with exactly one endpoint on .
Assume for the sake of contradiction that . Since there are at most edges with exactly one endpoint on , there exist two non-adjacent nodes on that have degree less than . Adding an edge between these two nodes to would decrease the effective path length, which contradicts the optimality of . Moreover, since and were chosen arbitrarily, it holds that for all pairs with non-zero demand the distance between and in is . By minimality of , it follows that has at most nodes.
NP-completeness for .
For degree bound one can easily observe that, for both versions of the bounded-degree network problem, there is an optimal host graph that is a collection of cycles. Moreover, it is clear that Steiner nodes cannot improve the solution for .
Avin et al. [8] have noted that for connected demand graphs, the bounded-degree network design problem for is very close to minimum linear arrangement. More precisely, we can reduce from the undirected circular arrangement problem, known to be NP-complete [29], to prove that bounded-degree network design problems are NP-complete:
- Instance:
-
Graph with , a weight function , a positive integer .
- Question:
-
Is there a bijection such that
where .
The circular arrangement problem can be seen as an instance of bounded-degree network design where the host graph is required to be a cycle. In particular, circular arrangement is equivalent to bounded-degree network design with on connected instances, as in that case the host graph is also required to be connected – i.e., a path or a cycle. Thus, the NP-completeness for both versions of bounded-degree network design follows from the following observation:
Lemma 11.
Undirected circular arrangement problem is NP-complete when restricted to connected graphs.
Proof.
Membership in NP is trivial. For NP-hardness, we reduce from undirected circular arrangement on general inputs.
Let , and be an instance of undirected circular arrangement. We construct a new instance by letting be a complete graph on , and define the new edge weight function as
Finally, we set . Clearly is a connected graph.
First consider the case where is a yes-instance, and let be a solution satisfying . Using as a solution for and summing over the edges in , we have that . For edges not in , we have
Thus,
which is at most as the value of the sum is an integer. Hence, is a yes-instance.
For the other direction, assume that a yes-instance, and let be a solution satisfying . This implies that
Since all edge weights for are divisible by , the value of is also divisible by . This combined with above inequality implies
and thus we have
Hence, is a yes-instance.
NP-completeness for .
We prove NP-hardness for both variants of the bounded-degree network design problem. There are two main tricks we utilize in this proof, which we explain before proceeding with the proof proper.
First is the observation that when we construct instances for these problems, we can force any optimal host graph to have some specific edge we desire by giving this pair a large demand . If we then have edges we want to force, we can set the cost threshold of the instance to be between and , so that any valid host graph will necessarily include all of these edges.
The second trick is used to ensure that nodes in our gadget constructions have the desired degrees. We use the following simple lemma:
Lemma 12.
Let be an odd integer. There is a graph such that , one node in has degree , and all other nodes in have degree .
Proof.
We start from a -clique , and then remove an arbitrary matching of size . The resulting graph has nodes of degree , and 2 nodes of degree . We then add a new node and connect it with an edge to all the nodes of degree . The resulting graph clearly has the claimed properties.
We use Lemma 12 to do what we will henceforth call attaching a degree-blocking gadget: given a graph of odd maximum degree , some value , and a node with degree , we turn into a degree- node by adding copies of to the graph, and adding an edge between and degree- node in each copy of . Clearly then will have degree , and each added node will have degree exactly .
We now proceed to the main proof. For simplicity, we start with the case of odd maximum degree .
Theorem 13.
Bounded-degree network design and bounded-degree network design with Steiner nodes are NP-hard for any odd .
Proof.
We reduce from vertex cover on -regular graphs; recall that the problem is known to remain NP-complete even with the degree restriction [21, 20]. More precisely, we will give a reduction that has the additional property that the resulting instance is a yes-instance without Steiner nodes if and only if it is a yes-instance with Steiner nodes, thus proving NP-hardness for both variants of the problem.
Let be an instance of vertex cover (in its decision form, where we ask if there is a vertex cover of size ). We first define the various gadget graphs we will use in the the construction.
Selector gadget.
Let be the smallest power of two larger than . To construct the selector gadget, we start with a complete binary tree with leaves and root node . We arbitrarily select leaves as the selector nodes , and attach degree-blocking gadgets to each . We also attach degree-blocking gadgets to the root , and degree-blocking gadgets to the remaining leaves. One can now verify that each selector node has degree , and the remaining nodes in the selector gadget have degree .
Vertex gadgets.
For each vertex in the vertex cover instance, we construct a vertex gadget as follows – recall that by assumption has degree . We take a complete binary tree with leaves, denoting the root of the tree by . We identify of the leaves as terminal nodes for edges incident to node . Finally, we attach degree-blocking gadgets to the root , as well as degree-blocking gadget to each terminal node and degree-blocking gadgets to the remaining leaf.
Finally, we combine the vertex gadgets for all vertices in by identifying two terminal nodes for edge in the vertex gadgets of and , as well as merging the respective degree-blocking gadgets into one. We can now observe that in the graph formed by the combined vertex gadget, the root nodes for have degree , and all other nodes have degree .
Instance construction.
We now construct an instance of bounded-degree network design with Steiner nodes as follows. Let be the set of nodes in the selector gadget and the combined vertex gadgets as constructed above. For any edge in the gadget constructions, we set the demand to be . For each edge in the vertex cover instance, we add demand between the root of the selector gadget and the terminal node for . For all other pairs, we set the demand to . Finally, we set the effective path length threshold for the bounded network design instance to be , where is the total number of edges in the gadgets.
Correctness.
Now assume that is a yes-instance of vertex cover, and let be a vertex cover. Let be a host graph for instance obtained by taking all the gadget edges and edges for . The demands for the gadget edges are satisfied by with direct edges, contributing a total of to the effective path length. Now consider an arbitrary edge and a demand between and . Since is a vertex cover, there is a vertex such that the edge belongs to . Thus there is a path from to in that starts from and travels along the selector gadget to , crosses the edge and travels from to along the vertex gadget for . This path has length . Since was selected arbitrarily and is a vertex cover, this holds for all edges . Therefore the total effective path length is , that is, is a yes-instance.
For the other direction, assume that is a yes-instance, and let be a host graph with effective path length at most . First, we observe that must include all gadget edges, as otherwise the effective path length from the corresponding demands is at least . Now consider the path between and for an arbitrary . Since all gadget edges are included in , this path must exit the selector gadget via an edge connected to one of the selector nodes , as all other nodes in the selector gadget have degree from the edges inside the gadget. By the same argument, the path must enter the vertex gadget via one the nodes and travel via gadget edges to . It follows that this path must have length at least . Thus, for the effective path length to be at most , the distance between and each must be exactly .
We now observe that for an edge , by the same reasoning as above, the only way for the path from to to be of length is that the path travels from to a selector node , then from to either or by a direct edge, and then via the vertex gadget to . Thus, for any edge , either or is in for some . Thus, the set of vertices
is a vertex cover of , and since each may only be incident to one non-gadget edge due to the degree constraint, we have . Thus, is a yes-instance of vertex cover.
We can now modify the above construction for even maximum degree as follows.
Theorem 14.
Bounded-degree network design and bounded-degree network design with Steiner nodes are NP-hard for any even .
Proof.
Let be fixed and even. We start by taking the reduction given by Theorem 13 for , and modify it as follows. Let be the total number of nodes in the instance produced by the reduction, and let be the number of forced edges in the gadgets, i.e., the number of edges with demand .
We now create the instance for degree by taking two disjoint copies of the node set and demands of the degree- instance , and adding a demand for each pair of corresponding nodes from the two copies. All other demands for pairs from different copies is set to . Finally, the effective path threshold is set to .
If the vertex cover instance was a yes-instance, then the degree- instance has a solution of cost , obtained by taking the solution for degree- instance for both copies, and adding all the edges between corresponding nodes in the two copies. On the other hand, if the degree- instance is a yes-instance, then all high-weight edges between the two copies must be included in the solution, using up one edge for each node in the instance. Each copy of the degree- instance must have effective path length of for its internal demands, which by same argument as in the proof of Theorem 13 is only possible if the original vertex cover instance is a yes-instance.
Putting together all the results from this section, we obtain Theorem 4.
Appendix B Additional tables and figures
| Trace | entropy | cond. entropy | |||||
|---|---|---|---|---|---|---|---|
| fb-cluster-rack-A | |||||||
| fb-cluster-rack-B | |||||||
| fb-cluster-rack-C | |||||||
| hpc-cesar-mocfe | |||||||
| hpc-cesar-nekbone | |||||||
| hpc-boxlib-cns | |||||||
| hpc-boxlib-multigrid | |||||||
| p-fabric-trace-0-1 | |||||||
| p-fabric-trace-0-5 | |||||||
| p-fabric-trace-0-8 |
| Trace | EPL | EPL | EPL | |||
|---|---|---|---|---|---|---|
| fb-cluster-rack-A | ||||||
| fb-cluster-rack-B | ||||||
| fb-cluster-rack-C | ||||||
| hpc-cesar-mocfe | ||||||
| hpc-cesar-nekbone | ||||||
| hpc-boxlib-cns | ||||||
| hpc-boxlib-multigrid | ||||||
| p-fabric-trace-0-1 | ||||||
| p-fabric-trace-0-5 | ||||||
| p-fabric-trace-0-8 | ||||||
